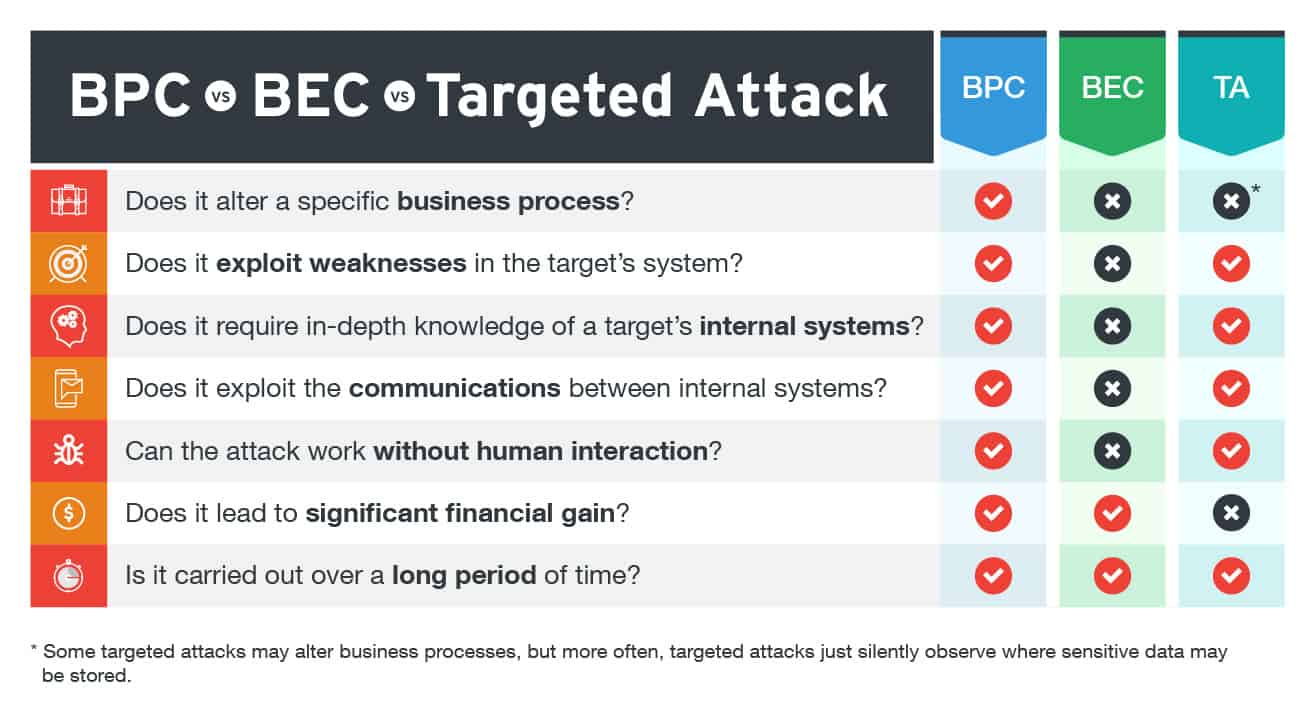
Business Process Compromise (BPC) is a form of cyber-attack that targets computer systems and networks. It is designed to disrupt, disable, or otherwise interfere with the normal functioning of a business process or its information systems. BPC attacks can be used to gain access to confidential data, cause physical damage to infrastructure, steal intellectual property, or compromise the system’s availability.
BPC attacks can come in a variety of forms, including system infiltration, malware and viruses, data theft, and denial of service (DoS) attacks. BPC attacks require a thorough understanding of the targeted system’s architecture, applications, and data in order to identify vulnerabilities. Once successful, the intruder may then attempt to hijack the system or commit data breaches, steal confidential data, gain access to restricted areas, or even cause physical damage to the system’s hardware.
BPC attacks also can leverage technology to conduct sophisticated activities such as injecting malicious code or scripts into a system, man-in-the-middle attacks, data ransom, and server-side request forgery. To thwart these attacks, personnel must employ appropriate security measures such as updating the software, deploying layered defenses, and monitoring system activity.
Business Process Compromise attacks pose a serious threat to organizations, as they can have a severe impact to not only the systems and networks but also the business operations as a whole. BPC attacks can cause financial loss, brand damage, the destruction or theft of property and data, and disruption to operations. Therefore, organizations must take appropriate preventive measures such as having a good security culture, establishing clear security policies, and using appropriate cyber security tools.