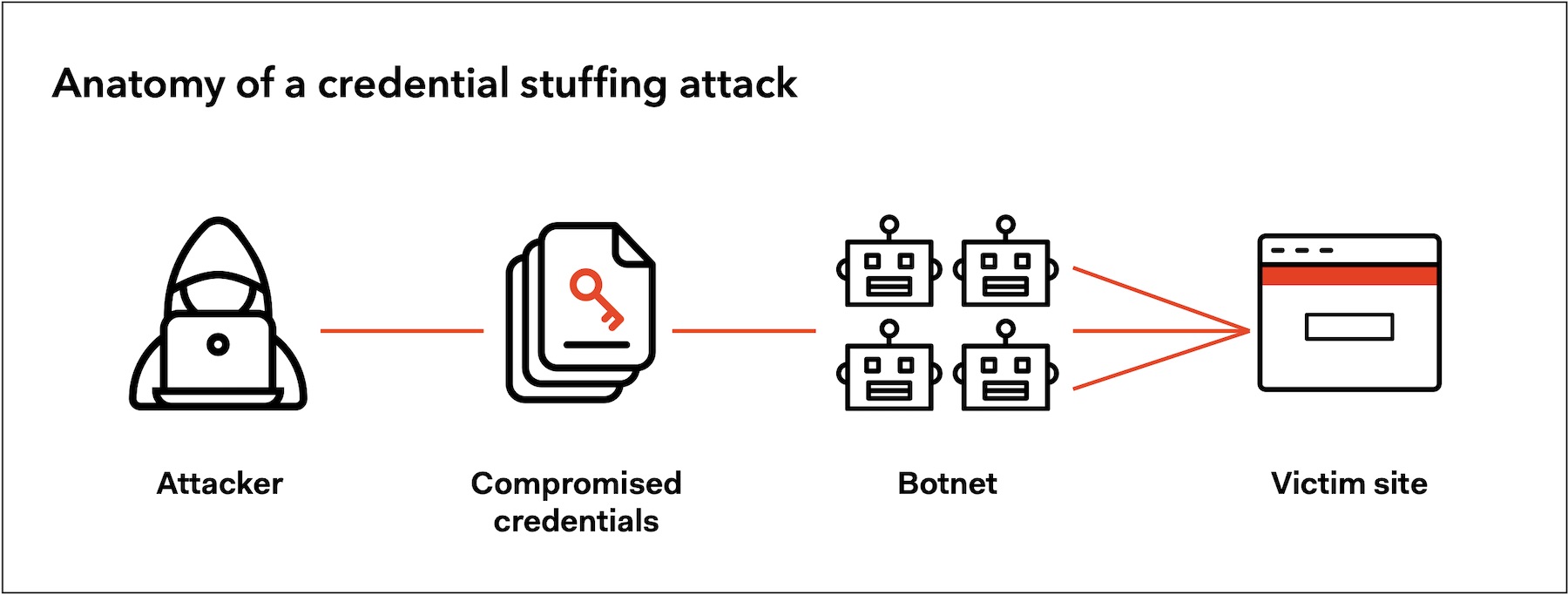
Credential Stuffing is a type of cyber attack that uses stolen username and password combinations to gain access to private networks and online accounts. It is a form of automated brute force attack, where a scheme is used to try and gain access to services using previously acquired credentials that have been obtained through various means, such as phishing or data breaches.
The aim of a credential stuffing attack is to take advantage of the tendency of people to reuse login details across multiple online services, and to exploit the details that are often seen to be stored on databases that are relatively easy to access.
Credential stuffing attacks tend to involve attackers attempting to access accounts by using large lists of previously compromised usernames and passwords, which are automaticall y fed into a computer program and used to guess login credentials. The attacks can be targeted at any online service that requires a username and password to access.
When a username and password pair that is part of the automated list is found to be correct, it then allows the attacker to gain access to the account. They will then typically use the account for some kind of malicious purpose, such as to harvest further logins credentials, commit further cybercrimes, or even spread malicious software.
In order to protect yourself against credential stuffing attacks you should always ensure that your passwords are unique for every website and account you create. It is also important to ensure that your passwords are strong and complex, and not easy to guess. Additionally, using two-factor authentication for your accounts can help to protect you against credential stuffing, since it requires users to enter more than just a username and password.