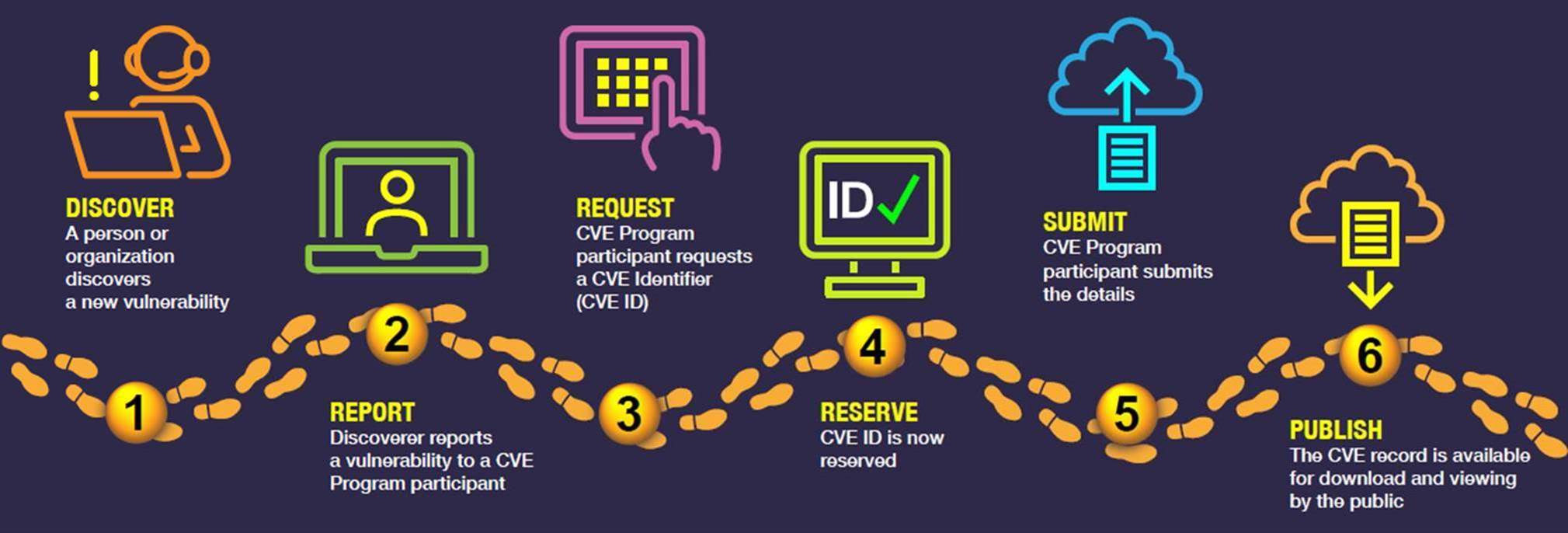
CVE Identifier (previously known as CVE Number) is an identification system for publicly known computer security vulnerabilities or exposures. It was created in 1999 by the United States government’s MITRE Corporation’s CVE team as a response to the growing severity of security incidents. The number is assigned by a piece of software called a CVE Identifier Generator, which indexes and assigns CVE ID numbers for any known vulnerability or exposure.
A CVE Identifier is usually in the format CVE-year-number. For example, CVE-2020-3463 is a valid identifier for the year 2020. This number will never be re-used and can be universally applied across different operating systems, software, or hardware. It is sometimes also known as a CVE Number.
The goal of a CVE Identifier is to provide a standard and consistent way to refer to known software security vulnerabilities, making it easier for IT departments to reference the issue and automatically track and report vulnerabilities. A CVE Identifier is composed of standardized details about the vulnerability or exposure, such as its name, description, and severity or risk level.
The identifier system is open-source and freely available to the public, making it one of the most widely used standards for security incident identification. It is used in a variety of ways, including security research, vulnerability management, and other tracking and reporting tasks. The identifier system is maintained by MITRE Corporation’s CVE team and is updated frequently with newly discovered vulnerabilities.
All organizations and users of computer systems who seek to protect their technology and data are encouraged to use and reference CVE Identifiers when discussing known security issues. This way, organizations can help ensure awareness and quickly roll out action plans to patch the exposed vulnerability. For reference, the official CVE list can be found at https://cve.mitre.org/.