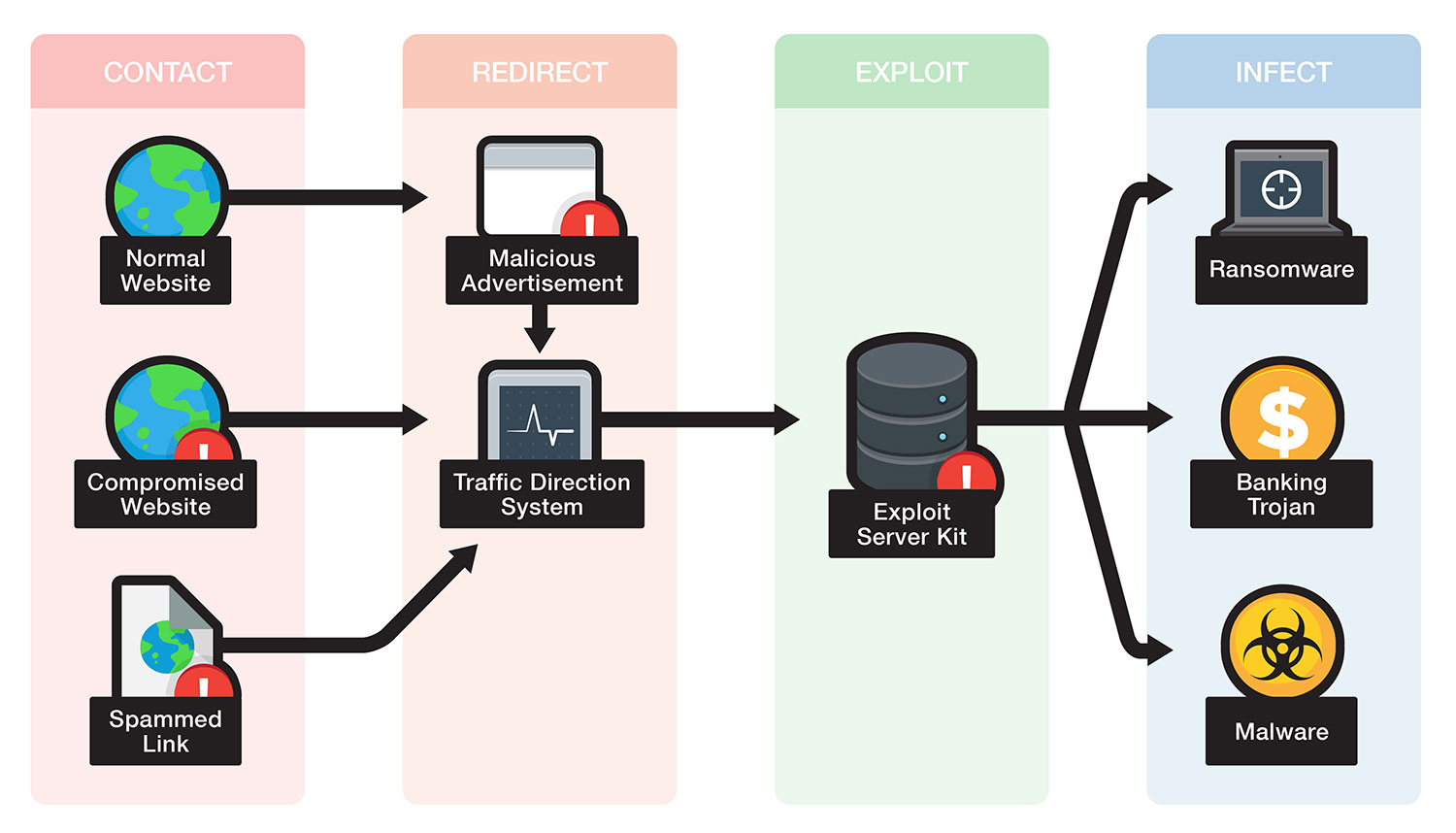
Exploit kits, also known as crimeware kits, are a type of malicious software used by cybercriminals to automate the delivery of malware such as viruses, worms, and Trojans to unsuspecting users. Exploit kits are usually distributed through malicious websites that contain malicious code that exploits one or more vulnerabilities in a system, and then downloads and executes malicious code on the affected system. Exploit kits are typically used to distribute malware for financial gain, such as bank account theft, ransomware, and various other types of fraud.
Exploit kits usually include tools that help malicious actors assess the security of the target system, generate malicious code, manage the malicious code or payload, as well as bypass security measures such as antivirus software. Some exploit kits also provide a platform for attackers to develop custom payloads, which allows them to tailor their attack against specific targets.
Common types of exploit kits are Blackhole, Cool, Phoenix, Nuclear, Fiesta, Carberp, and RedKit. These kits often come bundled with exploits for multiple applications and operating systems, including Windows, Mac OS X, Linux, and various mobile platforms.
Exploit kits are used in targeted attacks against corporations and organizations, as well as in mass-mailed campaigns. In the latter case, they are usually combined with malicious Web links or attachments, which when clicked, install the exploit kit on the target’s machine. Exploit kits are also frequently used to distribute ransomware, which blocks access to the user’s data unless they pay a ransom.
Due to the increasing prevalence of exploit kits and the sophistication of their functions, it is important for computer users to be aware of the threats that these tools pose. Installing security patches, using anti-malware software, and avoiding suspicious websites and links are some of the best ways to protect yourself from exploit kits.