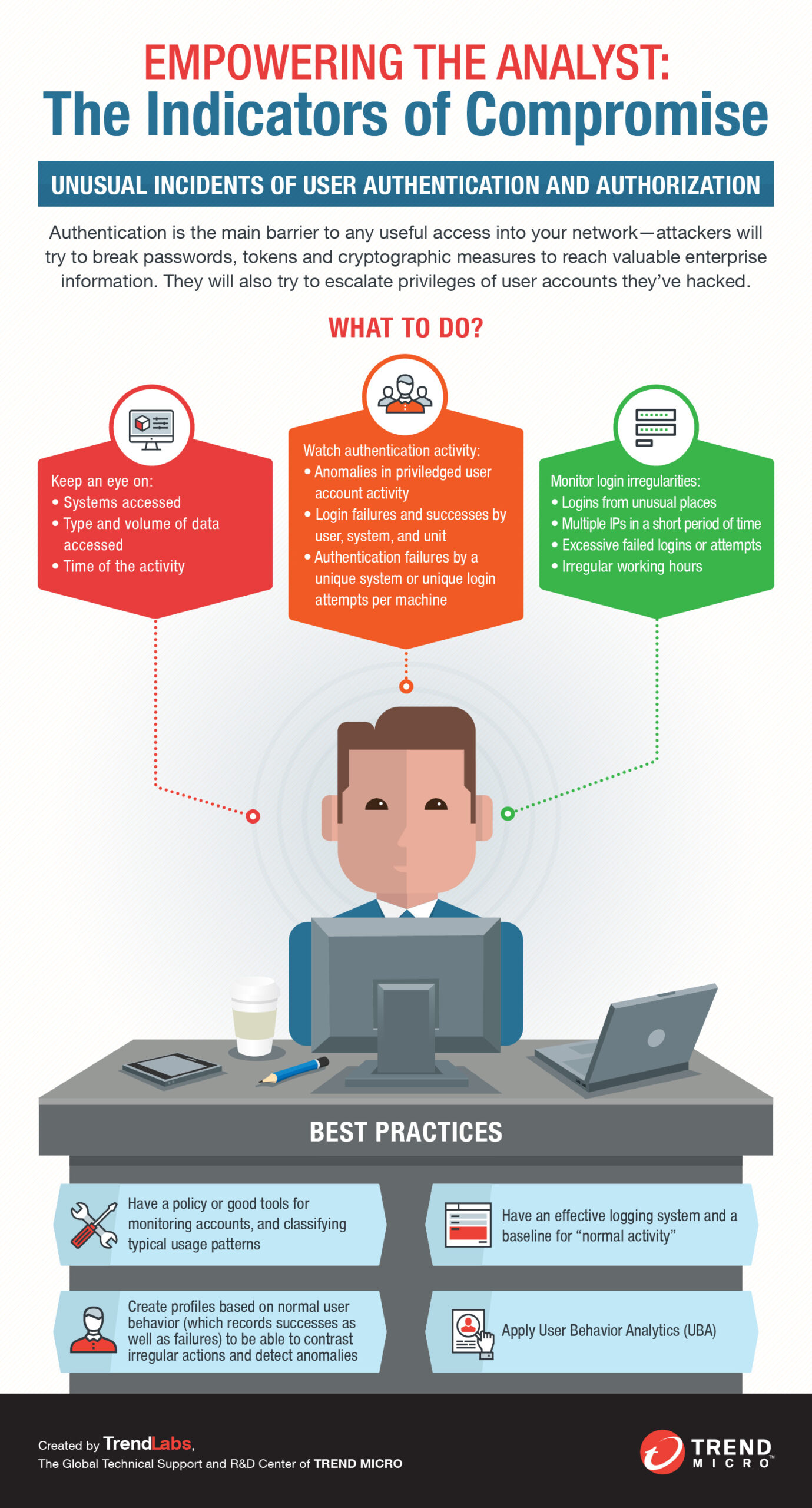
Indicator of Compromise (IOC) is a term used to refer to any form of evidence or artifact that is detected on a computing system that can help to determine if a system has been hacked or compromised. This includes data and events that indicate malicious activity, such as malware execution, unauthorized changes to the system, or even attempted activities such as credit card fraud.
IOCs are standardized digital forensic artifacts or evidence that can be used to detect, identify, monitor, investigate, and respond to cyber security threats or malicious activity, as well as to measure the effectiveness of any countermeasures. These artifacts may include IP addresses, domain names, file paths, hashes, registry entries, URLs, and other components of a digital forensic examination.
Examples of IOCs include:
* IP Addresses: An IP address is one of the most commonly used indicators of compromise. It can provide information about the originator and the destination of a network packet.
* URLs: A Uniform Resource Locator (URL) is a text string that identifies a network resource. Malicious actors may attempt to use URLs to conduct phishing or other attacks.
* Domain Names: A domain name helps to identify the owner of an IP address and may be used to detect malicious activity.
* File Paths: Malicious files may be identified by examining the file path of the data.
* Hashes: Cryptographic hashes are created to identify unique files and binaries. They can then be used to detect malicious files or tools.
* Registry Entries: Registry entries on Windows may contain clues to the presence of malicious activity.
When used correctly, IOCs can help to detect, identify, investigate, and respond to cyber security threats. Although they can provide useful and sometimes substantial evidence of a breach, they should not be relied upon blindly. Research and deeper analysis may be needed to properly assess the underlying risks and make decisions about how to respond.