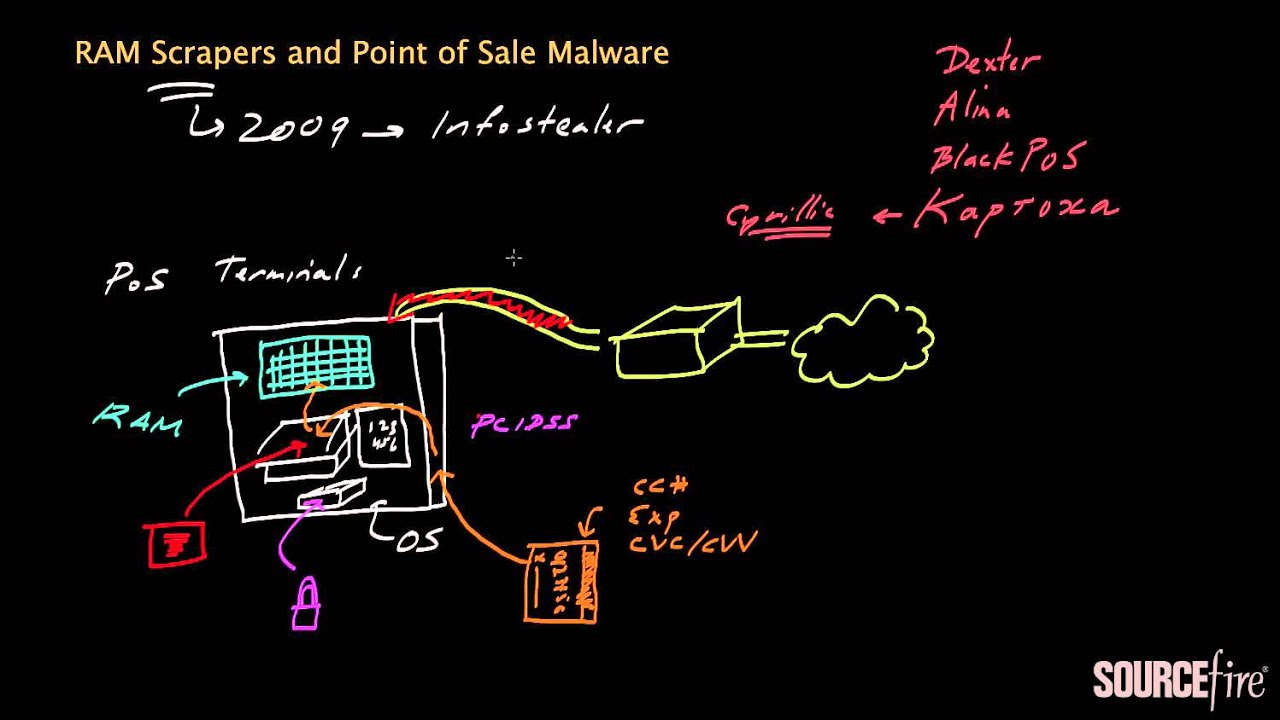
RAM scraping is a computer security technique used by attackers to steal secure information stored in a computer’s volatile memory or RAM. The data stolen may include passwords, encryption keys, cookie data, credit card numbers and other sensitive data.
This method of stealing data is effective because RAM is used to store data temporarily, so attackers can take advantage of this in order to steal data without leaving any evidence in the computer’s hard drive. As RAM does not exist on the computer’s hard drive, attackers can evade discovery as this type of data is not typically logged.
This technique can also be used to bypass security measures such as firewalls and ssl encryption. Attackers use software to bypass these measures by searching RAM for information, which is not protected by encryption or other security measures.
In order to protect against RAM scraping, organizations should ensure that any confidential data stored in RAM is encrypted with strong encryption algorithms. Additionally, organizations should keep their systems patched and up to date, as many of the tools used to perform RAM scraping can take advantage of vulnerabilities in an unpatched machine.
In summary, RAM scraping is an effective method of stealing confidential data from a computer. It is effective because it allows attackers to bypass security measures such as firewalls and ssl encryption. To protect against it, organizations should ensure that all confidential data stored in RAM is encrypted and that systems are kept up to date.