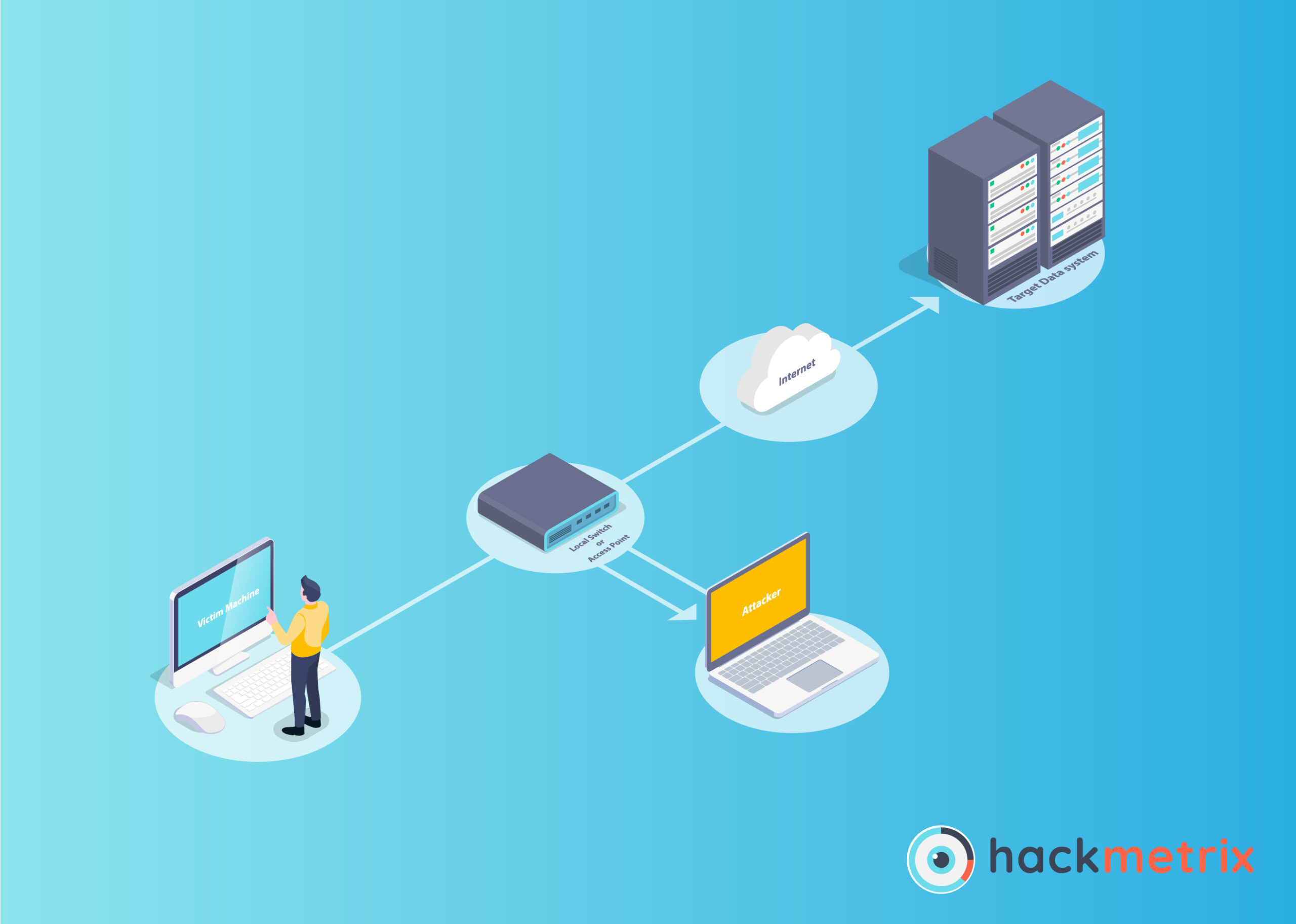
Remote Code Execution (RCE) Attack
Remote Code Execution (RCE) is a type of computer security vulnerability that allows attackers to remotely execute malicious code on a target system. It is one of the most serious attacks, as it can allow an attacker to completely take control of a system, render it useless, access confidential data, or even delete files or services. It can also be used to spread malware or create botnets.
RCE attacks are particularly dangerous due to their remote capability; a malicious actor can launch one without being physically present on the target system. The attacker can scan the network for vulnerable systems, then send malicious code to the target system via multiple methods such as web requests, command-and-control (C&C) servers, operating system calls or exploiting vulnerable applications or browsers.
The most common way to prevent RCE attacks is to ensure that your systems are up-to-date and that all applications and browsers are patched. Systems must also be configured to protect against external threats and accounts should be monitored regularly. Additionally, input validation should be enabled to screen for malicious input and access should be limited to authorized users only.