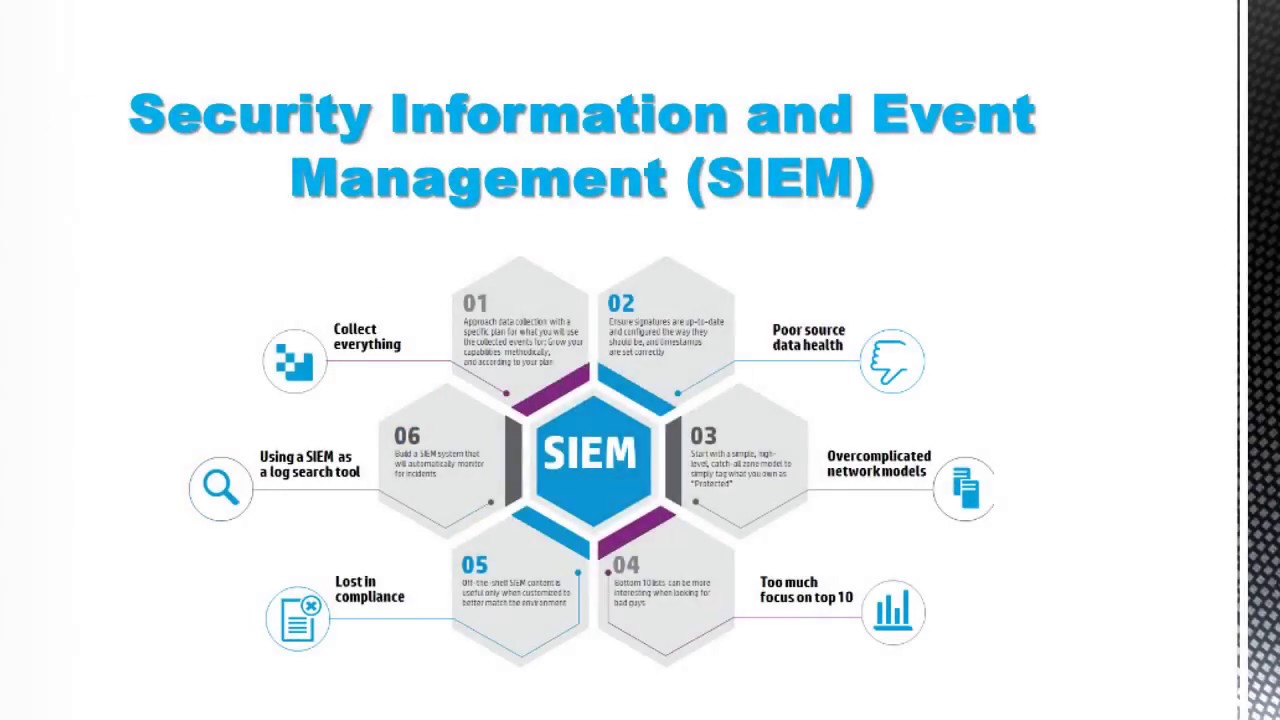
Security Information and Event Management (SIEM) is an approach to information security management used to identify and address events and incidents. It combines real-time monitoring and analysis of security alerts and log data from multiple sources across an organization’s networks, systems, and applications. Security Information and Event Management (SIEM) solutions integrate activities like log management, security event management, incident response, and compliance into a unified platform.
SIEM technology allows organizations to identify and defend themselves from cyber security threats and potential data breaches by providing real-time visibility and control over their IT systems, networks, and processes. SIEM security solutions analyze and process events in order to identify incidents that require attention, alerting and responding to security events in real time. The ultimate goal of SIEM technology is to improve the security posture of an organization.
SIEM solutions use artificial intelligence and analytics to reduce the rate of false alarms as well as particular patterns in network activity that require human analysis. This type of security monitoring and analysis increases the accuracy and speed of responding to security threats.
SIEM can be integrated with other security solutions in order to enhance their effectiveness. For example, a SIEM can be combined with Endpoint Detection and Response (EDR), vulnerability management, application security, and other solutions to create a more comprehensive security environment.
SIEM solutions are highly scalable and configurable. Organizations can be up and running in a few days, and they can choose the type and amount of data they need to monitor and process.
SIEM is an important asset for organizations of all sizes as it helps them detect and respond to cyber threats quickly and effectively. The technology continues to evolve as organizations search for new ways to maximize its capabilities and stay ahead of the ever-changing security landscape.