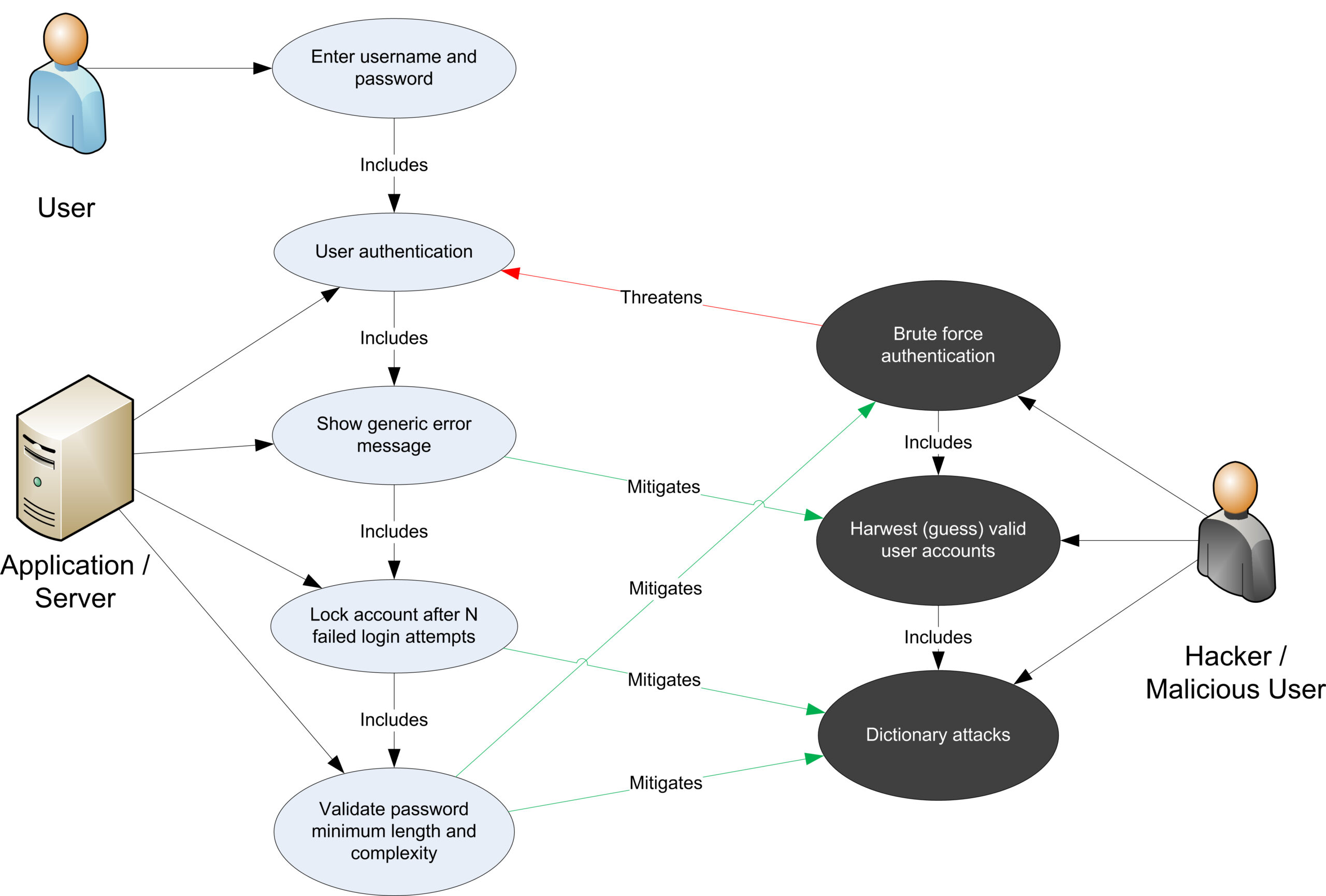
Threat model is a process used to identify, evaluate and quantify the security risks associated with a system, guide the selection of countermeasures, and enable trade-off decisions. Threat modeling is a key component of organizations’ overall risk management strategies.
Threats can be a wide variety of malicious intent or attacks such as those related to hacking, physical access, Man-in-the-Middle, worms, viruses, malware, and more. Most often, threat modeling is used to identify existing or potential security vulnerabilities and threats with the goal of detecting, preventing, and mitigating potential threats.
The process of threat modeling typically follows a methodical approach focusing on the three steps of identify, analyze, and design. The process typically begins with the identification of assets and stakeholders, the tracking of vulnerabilities, and the categorization of potential threats. The analysis step then focuses on defining threats, the likelihood of their occurrence, and evaluation of the impact on the asset. Finally, the design step focuses on solutions and countermeasures for each identified threat.
Threat model results are typically reported via a risk assessment document or a threat-profile matrix that are used to better inform decision-making on specific security solutions and countermeasures. Along with identifying potential threats, the process of threat modeling can provide a better understanding of how the system works, the various components and their interactions, and what operational mitigation strategies can put in place to improve system security.
Threat modeling is a critical component of risk assessment and management process, and helps not only identify and mitigate potential threats, but also helps ensure the security of the system against malicious attacks.