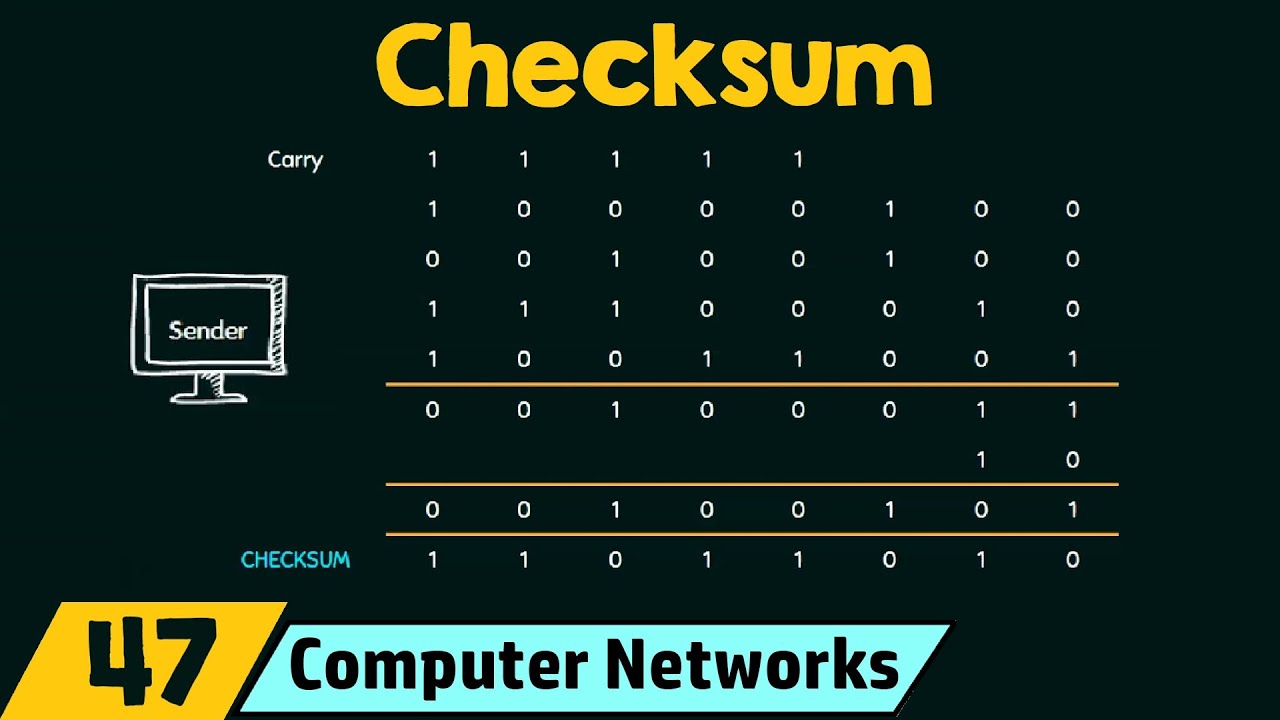
Checksum is a form of error-detecting code used in digital networks and storage devices to detect changes to raw data. It is used to detect accidental or malicious changes to data in a computer’s memory or data stored on a storage device. Checksums are widely used in modern computing for various purposes, most commonly to verify the integrity of a file or a data transfer.
A checksum is a small, fixed-length sequence of bits (or sometimes bytes) computed from an arbitrary block of digital data. A checksum is commonly used to verify data integrity, to ensure the data has not changed or corrupted in any way. Data corruption can occur due to a variety of factors such as transmission errors, environmental noise, software bugs, or malicious attacks.
Checksums can be used to detect such corruption in three main ways: (1) by comparing two file systems of different size, (2) by comparing two memory blocks of different size, or (3) by comparing two data streams of different size. Each of these comparisons requires an algorithm to calculate the checksum. Basic checksum algorithms include cyclic redundancy check (CRC), Fletcher’s checksum, Adler-32 checksum, and others.
The process of calculating a checksum is different from that used to calculate a hash as the latter usually takes a much longer amount of time, however the same algorithms can sometimes be used to calculate both. For example, a checksum can be calculated relatively quickly and used to ensure that a large file is error-free, but for strong security purposes a longer running hash algorithm might be employed.
Checksums are widely used in modern computing for various purposes such as network data integrity checks, file system data structure verification, digital signature verification, and code validation. Checksums are also used to detect malicious changes to data and various forms of malware.