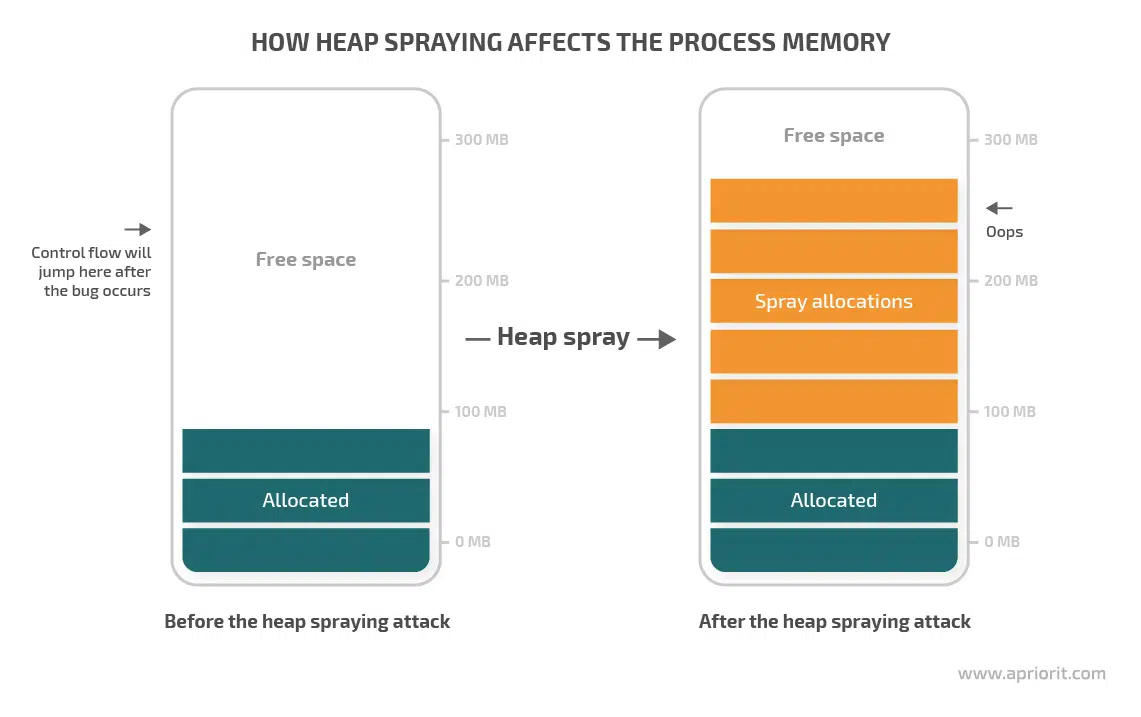
Heap spraying is a method used by malicious computer programs to bypass memory protection features implemented in modern computer operating systems. It works by filling up the memory with malicious code, effectively overwhelming the memory protection measures. Once the malicious code is in the memory, it can be executed, allowing the attacker to gain control of the targeted system.
Heap spraying was first documented in 2003 by security experts, who noted that the existing memory protection measures investigated at the time were insufficient. As attack techniques became more sophisticated, heap spraying became more prevalent. To counter this, numerous operating systems have implemented further memory protection measures, such as Address Space Layout Randomization (ASLR).
Heap spraying works by the attacker first identifying a vulnerability in the targeted system. Once identified, the attacker must craft malicious code that is designed to fit within the constraints of the exploited vulnerability, such as by using specific instructions or registers. The code is then repeatedly sent to the system via the vulnerability. As the code is accepted by the system, it is stored in the memory, taking up space in the heap. This ‘spraying’ of the heap can eventually cause it to become full, with the malicious code now occupying “holes” in the heap and thus avoiding detection from the operating system.
Once the malicious code is in the memory, it can be executed. This gives the attacker control of the system, allowing them to perform a variety of malicious actions, such as installing backdoors, collecting sensitive information, or launching further attacks.
Heap spraying is considered one of the most effective techniques used by attackers, since it enables them to bypass a variety of memory protection measures. As such, it is important that system administrators and security professionals remain vigilant, as newer technologies and techniques present a constantly shifting target for attackers to exploit.