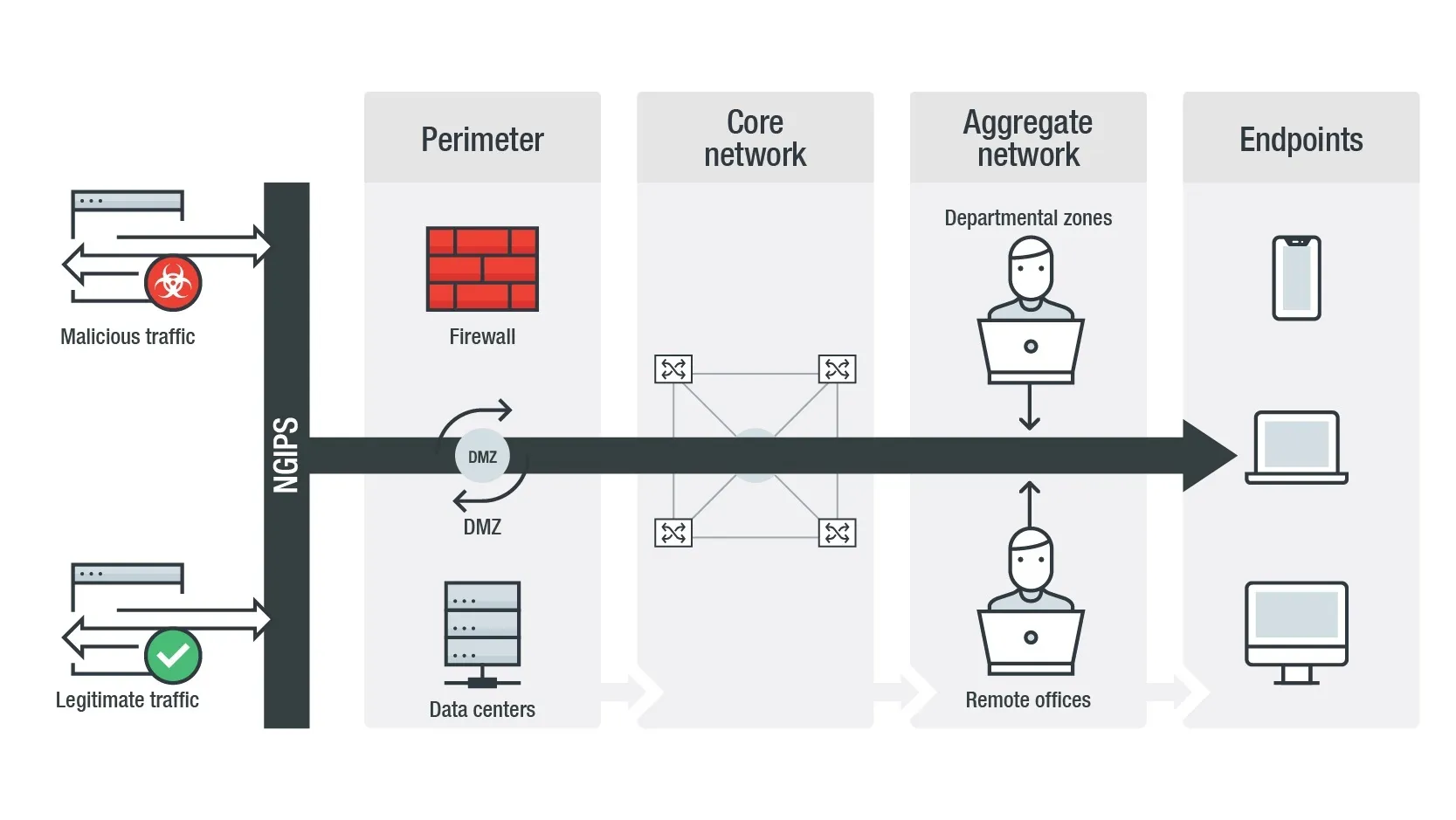
Network Perimeter
Network perimeter, also known as network boundary, is the boundary of an organization’s network, and is the collection of equipment and processes that define the boundary of the network and protect the resources of the organization from unauthorized access. The purpose of the network perimeter is to keep attackers from gaining access to the internal network, to protect the data assets, and to protect the organization from malicious traffic.
The network perimeter includes a combination of hardware, software, and network security policies. The most common components of a network perimeter are firewalls, routers, intrusion detection systems, and access control settings. Firewalls provide the first line of defense for an organization; they are designed to filter, manage, and block network traffic to and from a specific network. Routers are responsible for routing traffic from one network to another, and they can also be used to enforce network security policies. Intrusion Detection Systems (IDS) detect malicious or unauthorized activities taking place on the network, and can alert administrators or take corrective action. Finally, access control settings are used to restrict access to system resources and data to only authorized personnel.
Having a strong network perimeter is essential for protecting an organization’s sensitive data and information systems from attack. Properly configured access control settings and network security policies can help limit the risks posed by external cyber threats, while firewalls and intrusion detection systems can be used to detect unusual activity and unauthorized access to resources. Therefore, it is important for organizations to regularly monitor and update their network perimeter to stay ahead of ever-evolving cyber threats.