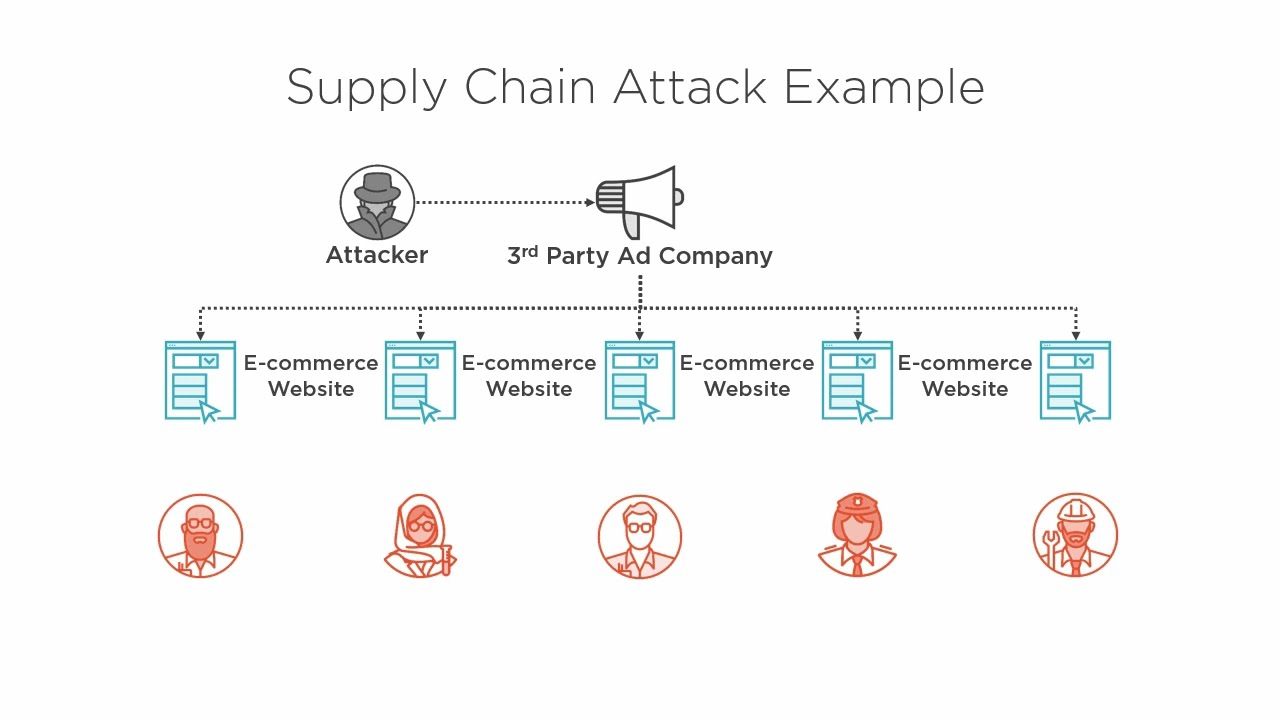
Supply-Chain Attack is a type of cyber-attack that attempts to gain unauthorized rights to networks and data by exploiting weaknesses in a system’s supply chain. This type of attack occurs when malicious code is inserted into an application or system at some point during the development process. The malicious code is designed to gain access to the inner workings of a system and can steal data or perform malicious activities.
A supply-chain attack can be used to gain access to a company’s system or network without permission. It can be used to steal data or take control of system components. It is also an effective way to launch attacks against third-party systems and networks. By exploiting weaknesses in a system’s supply chain, hackers can gain access to a system without the need for user authentication or authorization.
Supply-chain attacks are difficult to detect and can be difficult to mitigate due to the complexity of the system involved. In order to protect against these types of attacks, companies should ensure that their systems and networks are secure by following secure software development practices. They should also pay close attention to any changes in their supply-chain and take steps to address any potential weaknesses. Finally, companies should perform regular security audits to ensure that their systems and networks remain secure.