For the modern internet user, proxies serve as an important line of defense for ensuring personal security and anonymity in our data-centric digital landscape. But there’s no denying that navigating the world of proxy types can be technical – especially if you’re a newcomer to it. One such dilemma many come across is deciding between SOCKS Vs. HTTP proxy servers – how do you know which one is right for your use case.
To help shed some light on this question, we are here to explore what exactly these two different kinds of proxies mean and their key differences, so users can make informed decisions about deploying them effectively when necessary.
Table of Contents
- What are HTTP proxies and how do they work?
- What are SOCKS proxies and how do they work?
- 5 Reasons why you need SOCKS and HTTP proxies
- HTTP proxy vs SOCKS proxy: Main differences
- Which one is right for you?
- Conclusion
What Are HTTP Proxies and How Do They Work?
The main task of the most common type of proxy is the proper organization of the quality work of browsers that use the TCP protocol.
This type of proxy guarantee:
- caching downloaded files;
- limiting access to certain types of resources;
- Data filtering;
- limited connection speed;
- logging, and traffic control.
Types of HTTP proxies by anonymity:
- transparent: used to pass the user’s IP in HTTP headers. They’re not safe to use because they don’t give absolute anonymity;
- anonymous: report about proxy use, hiding real IP address. Doesn’t provide complete anonymity. The reason is the existence of proxy information;
- elite: do not inform about the proxy usage and do not show IP, they guarantee absolute anonymity.
Features of HTTPS Proxies
The HTTPS proxy is a more secure version of standard HTTP. The letter “S” that is added at the end stands for “Secure”. A secure SSL connection provides additional security to the proxy.
HTTPS servers are used when it is necessary to transmit secret information: credit card details, login/password, etc. If you use a standard HTTP proxy, there is a great risk that your data could be intercepted. Moreover, access to your information is of interest not only to intruders but also to ISPs. They track every step of their customers on the Internet, intercepting and logging all the information useful to them.
The HTTPS protocol can help keep personal data safe. When it is used, all transmitted traffic is encrypted using a special algorithm that is resistant to hacking.
How HTTPS Proxy Works
HTTPS connects to a web resource, which encrypts your traffic. In this case, the information transmitted through the proxy server can not be tracked. It is not the proxy that encrypts and decrypts the data, but the browser and the target server. Consequently, with HTTPS there is a passive transmission of encrypted information without any processing.
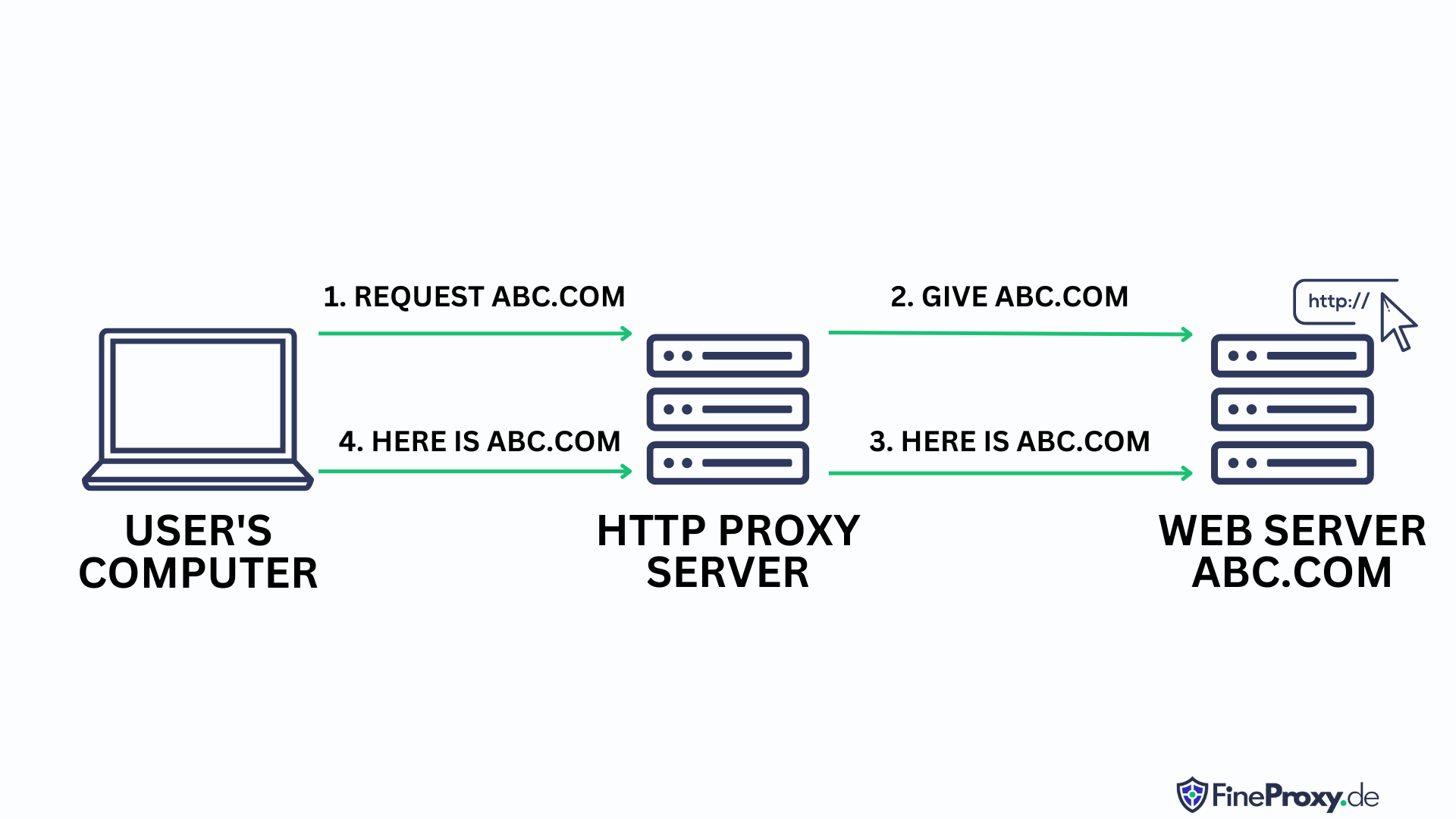
Due to this working principle, HTTPS can be used for almost any TCP protocol. The proxy can be used as IMAP, POP3, NNTP, SMTP.
Advantages of HTTP(S) Proxies
- HTTP(S) proxies provide a secure connection between the user and server, encrypting communication between them so that no third-party can intercept it.
- These proxies also grant users control over which web content they access by filtering data in order to protect against malicious activity. This is especially beneficial for businesses, as such security measures significantly reduce their risk when scraping data from multiple websites – without having to manually remove irrelevant or incorrect information afterward.
- By using an HTTPS proxy, companies are able to ensure accuracy of collected data while maintaining peace of mind regarding its safety.
Disadvantages of HTTP(S) Proxies
- In a world where online privacy is highly regarded, HTTP proxies fall short due to their inability to encrypt data, leaving users vulnerable to security breaches and exposed locations.
- Certain websites block HTTP proxies as a measure against automated bots and crawlers, hindering legitimate user access. The situation is further exacerbated by repetitive loading of the same webpage by diverse bots or terminals, resulting in an inefficient and frustrating user experience.
What Are SOCKS Proxies and How Do They Work?
SOCKS (Socket Secure) is a modern networking protocol that enables data to pass securely through firewalls, keeping communication between servers uninterrupted.
Unlike HTTP/HTTPS protocols which are more restrictive in their transmission capabilities, SOCKS does not modify any of the headers for requested information, allowing for swift and direct transfers. With ports 1080 & 1081 devoted exclusively to its service, it’s no wonder why this technology has become so popular; offering optimized support with programs incapable of handling regular proxies directly – making SOCKS4 and now 5 an everyday requirement when dealing with sensitive network traffic.
What differentiates ‘SOCKS5’ from ‘SOCKS’?
SOCKS is an essential protocol at Layer 5 in the OSI model, allowing for data requests and exchanges of a wide variety. These processes include HTTP, HTTPS, POP3 SMTP and FTP – all due to its ability to operate between SSL (Layer 7) and TCP/UDP (Layer 4).
For further clarification, it’s important to note that there are two primary forms:
- SOCKS4 which does not offer authentication;
- SOCKS5 which is more modernly-used with varying authorization capabilities. Additionally, unlike other versions this allows users access via User Datagram Protocol UDP proxies as well.
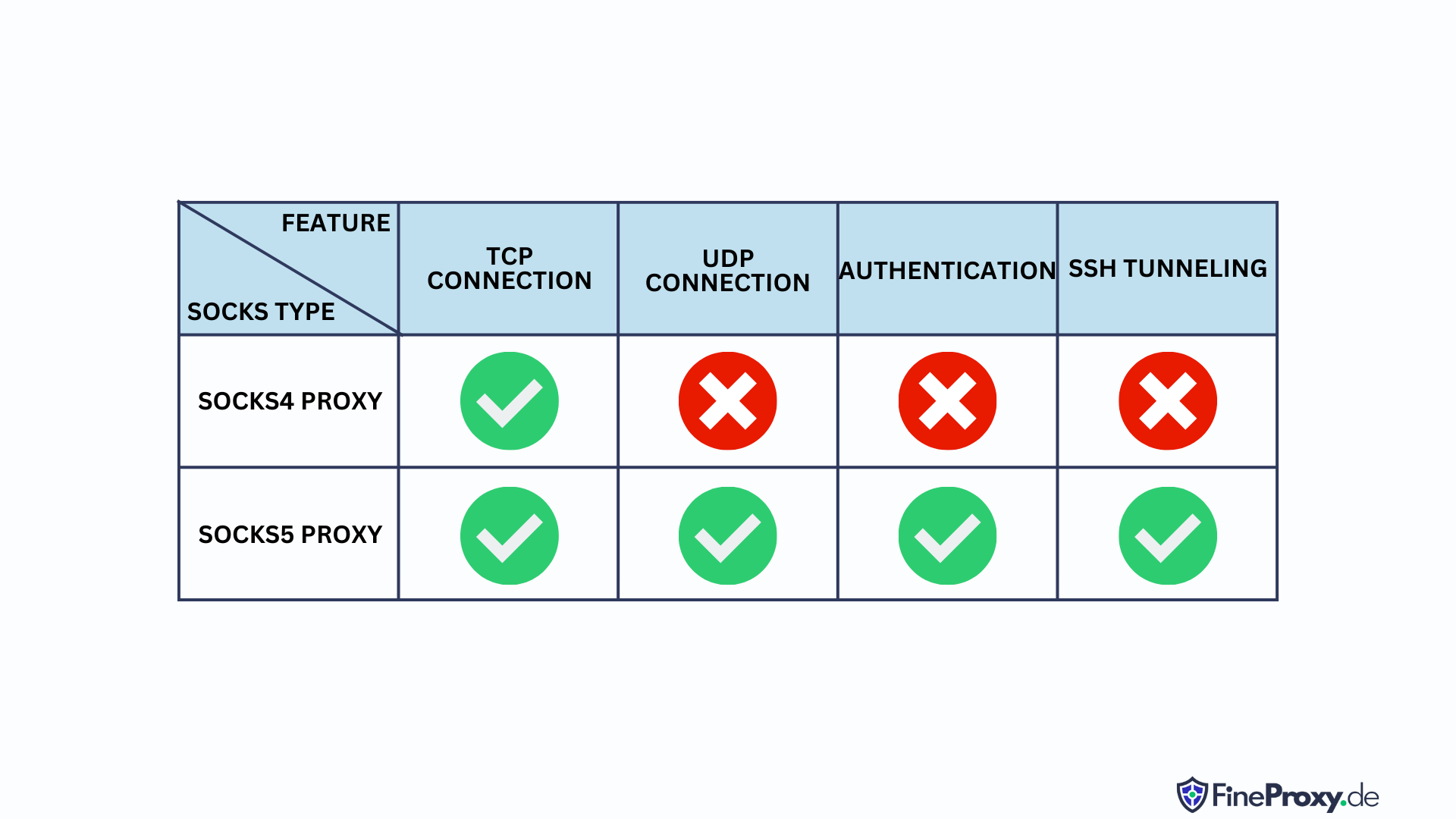
UDPs are a useful data transfer protocol that shines in scenarios where speed is the prime consideration. However, it cannot check for errors or order, which can be an issue when reliability of transmission matters more than quickness. Its connectionless mode has caused some security vulnerabilities due to lack of control over who accesses what information and how they use it.
How SOCKS5 Proxies Work
Socks does not moderate HTTP headers. These servers transmit information in the clear and are completely anonymous.
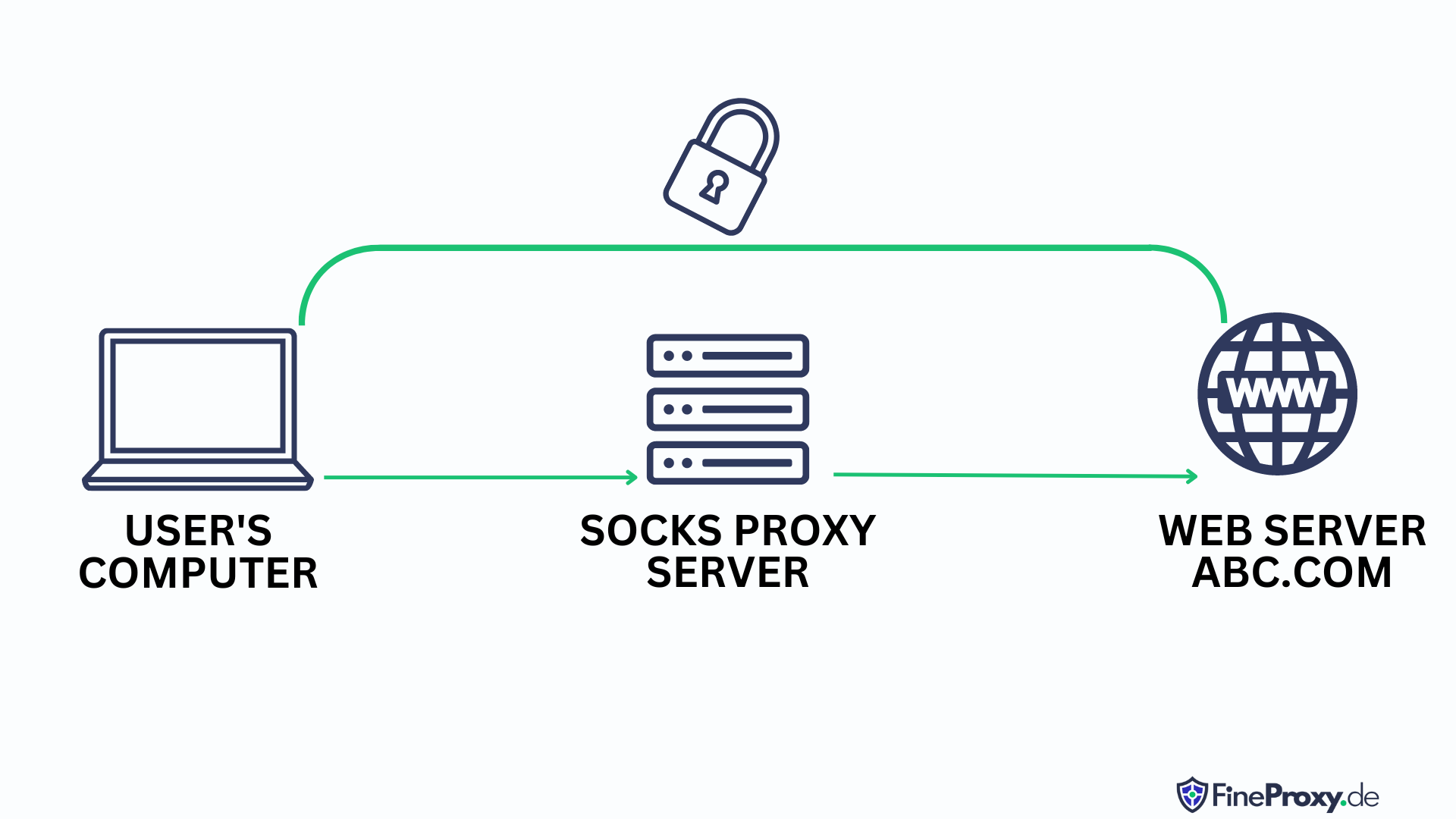
Information about the IP-address of the user when using SOCKS5 remains completely confidential. The site that you go to through this proxy can not determine that you used a proxy. The connection to the web resource is transparent, as if you had gone directly to it without using a proxy server. In this case, the site will show not your IP, but the address of the proxy used by you.
Socks supports all protocols, including HTTPS, HTTP, FTP.
Advantages of SOCKS4/5 Proxies
- A SOCKS5 proxy is faster than an HTTP proxy since it supports UDP connections. UDP is faster and more efficient than TCP.
- SOCKS5 proxies offer heightened security and speed compared to HTTP, thanks to their support for multiple authentication methods that help protect against malicious intrusions.
- They are capable of processing various protocols such as FTP and SMTP with greater efficiency due to the use of UDP over TCP connections.
Disadvantages of SOCKS4/5 Proxies
- SOCKS proxy, while advantageous in some aspects, comes with its fair share of limitations. For instance, it might test your patience with significant latency since all traffic must pass through the proxy server before reaching its ultimate destination. Additionally, accessing various websites might call for specific ports or protocols.
- Configuring a SOCKS proxy server can also be quite intricate, as it requires you to install and configure the server software on a computer, essentially making it your online sentinel. Moreover, keep an eye on expenses as setting up and maintaining dedicated public Socks proxies can be costly in the long run.
5 Reasons Why You Need SOCKS and HTTP Proxies
HTTP proxies offer businesses an ideal solution for a variety of situations, with their customizable server settings. There are countless advantages to using these valuable resources:
- HTTP proxies optimize data transfers, increase security, and improve the success rate of web scrapers.
- Acting as a middleman between client and destination, they understand what is necessary to be transferred – filtering out irrelevant material for content caching along the way.
- Additionally, advanced protection blocks malicious packets from entering servers while configuring request headers, making it easier to access restricted sites without being blocked.
For organizations looking to maximize the potential of their networks, SOCKS proxies are an ideal solution, and that is why:
- Firewalls can be a significant barrier to initiating TCP connections or accessing websites. SOCKS proxies are ideal for overcoming this challenge and allow clients behind firewalls the ability to make successful remote requests without restriction.
- They facilitate UDP connectivity that is capable of enabling fast delivery of data over any network protocol or port.
HTTP Proxy vs SOCKS Proxy: 7 Main Differences
Delve into the fascinating world of proxy types, where each contender has been meticulously crafted to champion unique use cases. In the epic battle of HTTP proxy vs SOCKS proxy, it’s not about which is superior, but rather mastering the art of recognizing when each triumphs in security and performance.
| Feature | HTTP | SOCKS |
|---|---|---|
|
1. Functionality |
HTTP proxies specialize in handling web-based traffic, offering configurable options like content filtering and caching web data to enhance your browsing experience | They are perfect for content streaming and P2P file sharing, owing to their protocol-agnostic feature. Unlike HTTP proxies, they don’t manipulate proxied traffic, making them ideal for bypassing firewalls and handling various network protocols with ease |
|
2. Security |
HTTP proxies introduce a protective layer between the client and server, effectively identifying and blocking dubious data packets or spyware | SOCKS proxies lack standard tunnel encryption |
|
3. Speed |
Private HTTP proxies excel in managing a higher volume of requests, keeping your online activities swift and smooth | Lightning-fast downloads and seamless data transfers with SOCKS proxies, which are the perfect solution for specialized systems and software clients |
|
4. Connecting with Tools |
HTTP proxy servers boast widespread connectivity | SOCKS proxy may offer limited device access |
| 5. Operability | While HTTP proxies may be restricted to a single protocol, their ability to analyze and identify discrepancies in cache requests and responses has made them quite useful | SOCKS proxies offer ease of use, compatibility with multiple protocols, and unique flexibility. Furthermore, SOCKS proxies excel in providing connection access even beyond firewalls, giving them an advantage over their counterparts |
| 6. Data Infiltration and Web Scraping | HTTP proxies possess the power to scrutinize network traffic, ensuring protection against compromised data and dubious activities. Experience seamless web scraping from giants like Google and Amazon, as your trusty HTTPS proxy interprets data for you prior to download, saving you valuable time | SOCKS5 proxies simply don’t match up to the dynamic capabilities of HTTPS proxies in data infiltration and network traffic interpretation |
| 7. Cost | When it comes to the cost of a proxy, both Socks proxies and HTTP proxies have available options which come in relatively cheap. For HTTP proxies, you can find providers offering plans that start at around $1/GB | As for Socks proxies, you can also find providers offering plans that begin at around $1/GB. That said, many users consider Socks 5 proxies to be cheaper than HTTPs over time since Socks also offers authentication while enabling multiple connections at once which allows for easier and more efficient use. Additionally, Sports 5 Proxies don’t need extra licenses for different applications or browsers. This means some significant cost savings when you need multiple connections from different devices and web browsers |
In the quest for the perfect proxying service, balance your desired anonymity level with efficient web interactions. After all, a tailored solution catering to your distinct needs paves the path for seamless browsing experiences. So, scrutinize and select the ideal option expertly.
In this video, the Oxylabs team explores the differences between SOCKS proxies and HTTP proxies. You’re also offered to take a look at some of the use cases for each type of proxy and when you might want to use one over the other.
Which One Is Right For You?
By carefully considering the security needs of your network, you can choose between a SOCKS5 and HTTP(S) proxy to take full advantage when configuring an internet proxy. The former is best for getting past firewalls without sacrificing safety while providing users with much-needed privacy and anonymity online. With so many options available, it’s important to weigh up which solution suits your individual requirements most effectively.
In the quest for the perfect proxy, ponder these crucial aspects:
- Data Dimensions: HTTP proxies play nice only with their own kind. Mixing in UDP, POP3, or other non-HTTP network data? Expect trouble. For versatility, SOCKS connections have your back, granting access to any data type.
- Speed Requirements: HTTP proxies zoom through data like a superhero, loading pages in lightning-fast time, while SOCKS proxies effortlessly manage connections with their no-code, easy-to-use approach.
- Price or Peril: The tantalizing world of free HTTP/HTTPS proxies invites you to play with the unknown. Will you gamble your safety and privacy for a costless experience? Beware, as hidden villains may lurk in the shadows, with viruses, malware, and secretive logs that chronicle your every move.
- Security and Privacy: Experience ultimate anonymity with SOCKS proxies, which refuse to log your actions, keeping your digital footprints undiscovered. Unlike their HTTP counterparts, SOCKS ensures no accidental sneaky peeks into your online escapades!
- Compatibility: SOCKS is a versatile solution that effortlessly supports both TCP and UDP transfer protocols, ensuring rapid access to any network. Unlike HTTP proxies that only cater to HTTP data, broad compatibility with a plethora of widely-used tools is guaranteed.
When faced with deciding between SOCKS and HTTP proxies, your best course of action is to consider what you intend to use it for. Each offers its own benefits in terms of increased security and anonymity – but make sure that the one which suits your needs gets chosen. With an understanding of both protocols’ advantages and disadvantages, you can ensure a more satisfactory online experience.
Conclusion
While HTTP and SOCKS proxies share many characteristics, the differences between them are impactful. Neither is clearly superior to the other, as they serve different purposes with specialized functionality.
The most widespread proxy type, HTTP offers an economical but insecure solution due to its ability to decrypt data from traffic passing through it. By contrast, a newer version of SOCKS – namely SOCKS5 – acts in a more secure fashion via authentication methods that do not involve the decryption of information passed through it.
In essence, when choosing your ideal proxy option for security and bandwidth considerations, you should weigh up both options carefully considering each scenario’s specific needs before making a decision.





