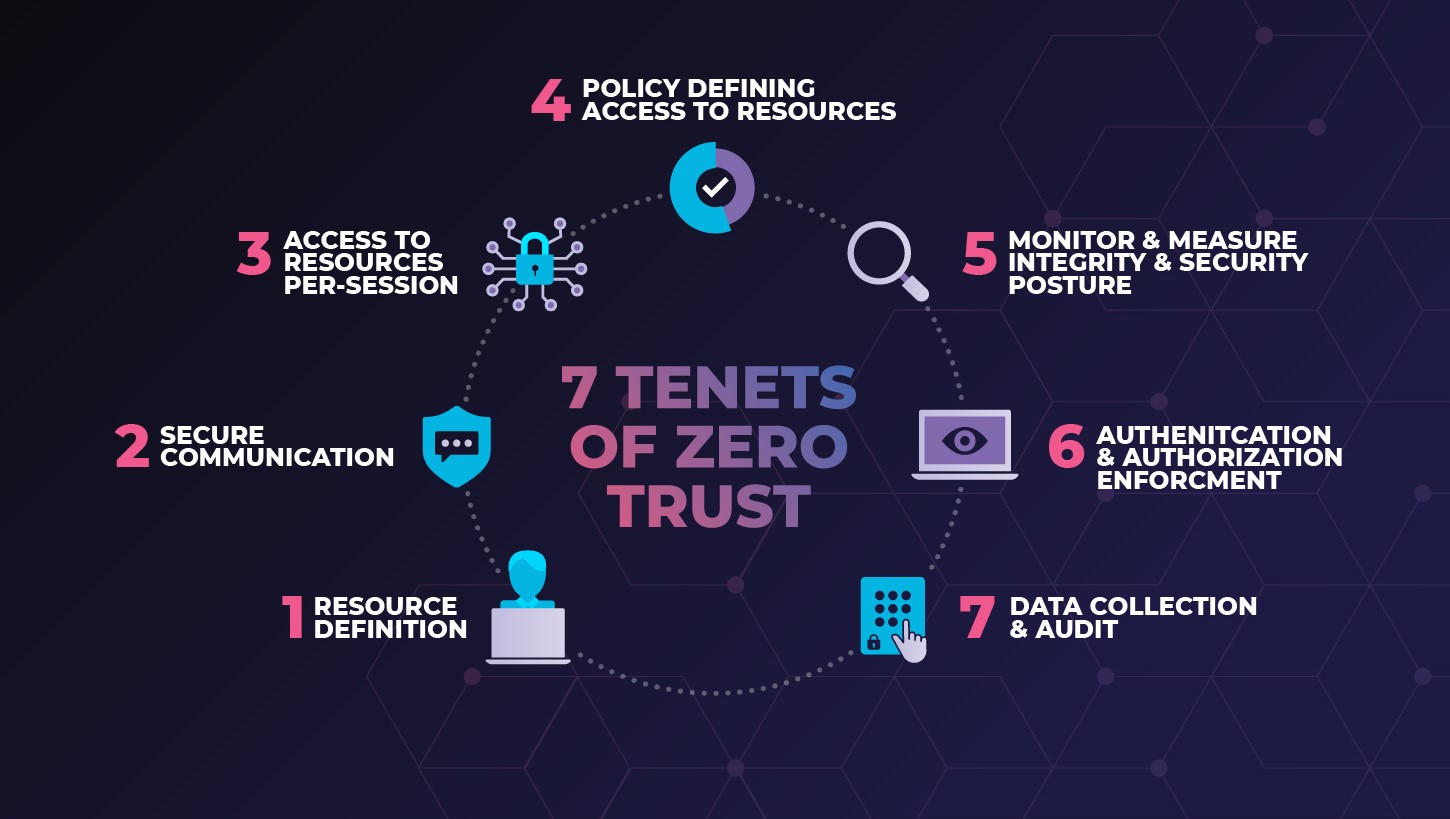
Zero-trust, or a zero-trust architecture, is a security philosophy used by enterprises to protect their networks and systems from potential cyberattacks. It is based on the idea that nothing, including trusted internal actors, can be assumed to be trustworthy or legitimate. Under zero-trust, organizations access control systems will assume that all users, applications, and network communications should be treated as untrustworthy and subjected to strict verification and authorization procedures.
Organizations implementing zero-trust will deploy strict identity and access management (IAM) controls, such as two-factor authentication, to ensure that only authenticated and authorized users can access the network. Furthermore, zero-trust systems will also track user activity and analyze the outcomes of user actions for any suspicious activity. This system is used to provide granular, contextual access control and monitor user activities.
In addition to identity verification, zero-trust systems will also strictly limit network access by segmenting infrastructure and only allowing users access when, and where, it is necessary. This segmentation is further enhanced through micro-segmentation, which looks to further limit access to specific components of the network, and application-layer segmentation, which restricts access to specific applications.
Zero-trust architectures are being adopted by enterprises to help protect their systems and networks from potential security threats. By only allowing users access when necessary, having granular contextual access controls and monitoring user activity, zero-trust systems not only provide an extra layer of security, but also limit the window for any potential attack or incident.