Vulnerabilities
Vulnerabilities refer to weaknesses in computer systems that can be exploited by attackers. They are caused by weaknesses in the system, either by exploiting a flaw in the software or hardware, or exploiting settings and configurations that are insecure.
Vulnerabilities may be classified into two categories: known vulnerabilities (also called “vulnerability windows”) and zero-day exploits (also known as “new” or “zero-day” vulnerabilities). Known vulnerabilities are weaknesses that have already been identified and documented, including security-related flaws or flaws caused by misconfiguration. Attackers are aware of such vulnerabilities and use them to exploit computer systems. Zero-day exploits are newly discovered vulnerabilities and usually are not publicized or disclosed until after they have been used to attack systems.
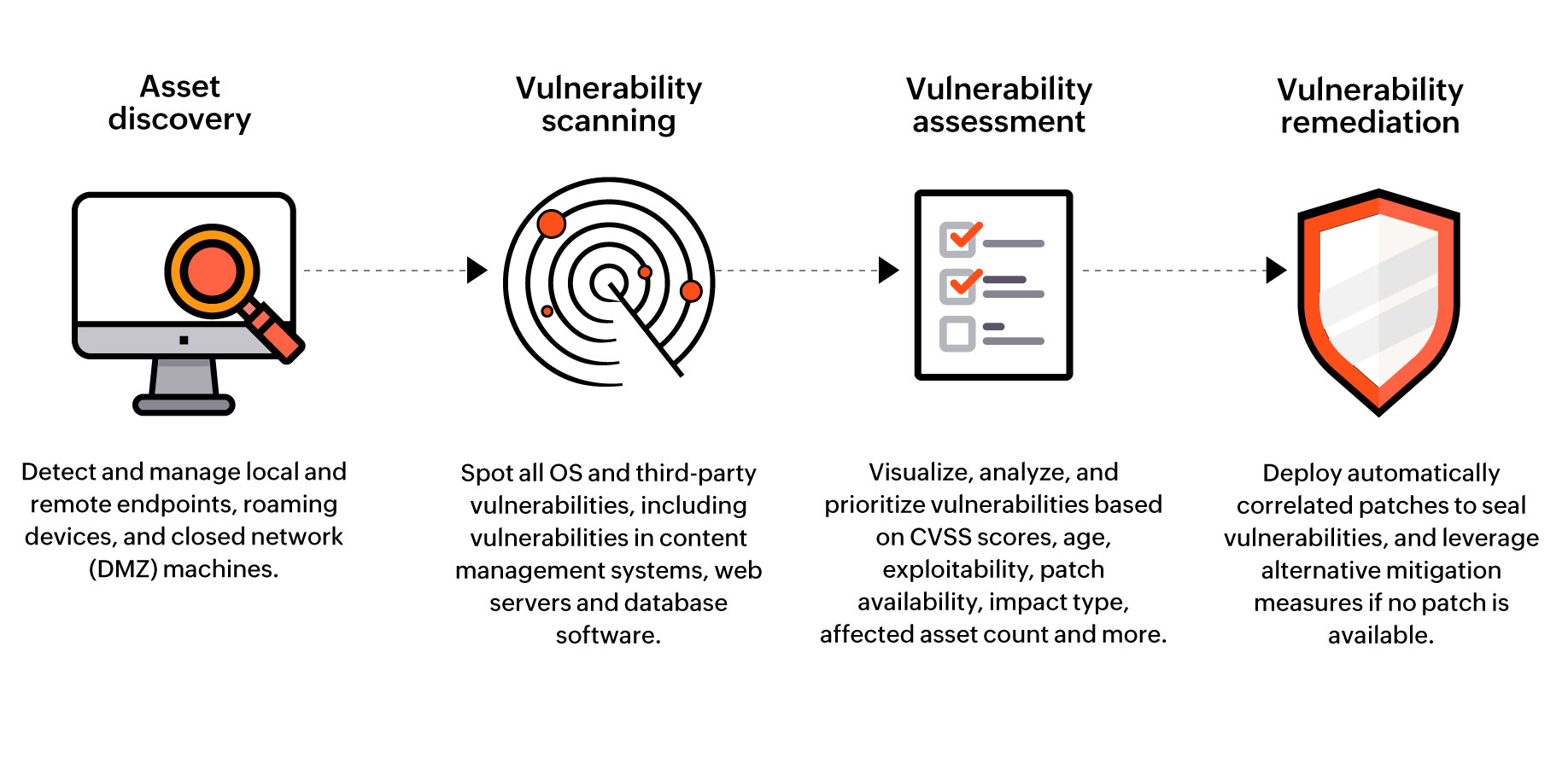
When a vulnerability is found, the responsible software or hardware provider is tasked with creating a security patch or program update to address the problem. It is critical to apply the patch or update as soon as possible, as attackers could attempt to exploit the vulnerability. Additionally, security best practices should be implemented and regularly updated to ensure continued security.
Organizations must stay vigilant and proactive in order to protect their systems. Regular vulnerability scans, penetration testing, and updates to security policies and procedures can help minimize the risk of attackers leveraging a vulnerability in their system.
Vulnerabilities continue to be a major security threat in the ever-evolving landscape of technology. Organizations and individuals must remain diligent in their efforts to ensure the security of their systems and networks.