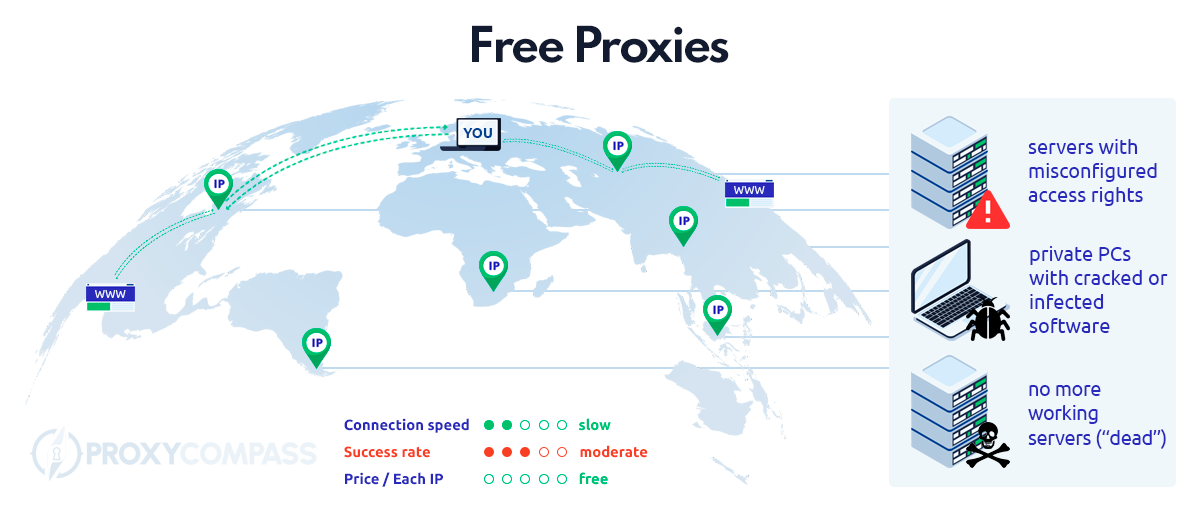
So-called “free” or “public” proxies are freely accessible lists of IP addresses published on various online resources.
Where Do Public Proxies Come From?
Public proxies can come from different sources.
First example: An inexperienced server administrator (e.g. an administrator in an educational institution) installs a proxy script for the institution’s requirements, but does not change the default ports (80, 3128) and does not secure them with a password. In this case the institution’s server becomes a public proxy.
Second example: An Internet user downloads a program that contains a security hole and cannot be updated because the copy protection has been removed (“cracked software”) or a Trojan has been installed. In this case the private computer becomes a public proxy.
All these servers and private computers are now accessible from the outside. This means that if you know their IPs and the port where the proxy is open, this remote computer can fulfill the function of a proxy, i.e. you can send and receive requests to other servers through it.
Where Free Proxies Originate
The ranges of IP addresses are scanned using programs like Charon, usually from similarly infected servers. Attention: This is illegal and there may be legal consequences for such activities. The IP addresses are then used to send spam via SMTP ports as well as for brute force and DDoS attacks.
After such proxies become unusable (i.e. when their IPs are added to the spam database), they are often published in unrestricted forums.
It is strongly discouraged to use such proxies to transfer important data: e.g. for social networks, instant messengers and especially to conduct financial transactions.
Who Uses Public Proxies?
Despite all the risks associated with the use of public proxies, they are in great demand among SEO specialists. Because usually Google does not manage to block them and they can be used to parse search results.
You can find a list of such proxies on the page with free proxies.
However, there are also online services that offer lists of IP addresses for money. These proxies are usually collected with the help of parsers in well-known proxy forums and other websites.
Prior to the sale, the list is checked for duplicates and availability, sorted by geo-location and protocol and sent to the customer.
Disadvantages of Free Proxy Lists
Potential buyers of such lists should be aware that services offering such lists have no control over the listed proxy servers. It is impossible to check for which purposes and by how many people such proxies have already been used.
Such proxies typically do not have a long “life span” ̶ usually until the server administrator or computer owner notices an unusually high load and closes the security hole (or simply reinstalls the system).