It is very easy to hide your IP address, and this has a number of advantages, especially now that online tracking has reached its peak. There are many ways to hide the actual IP address of your device, but when do you need this?
Why does the IP address have to be hidden?
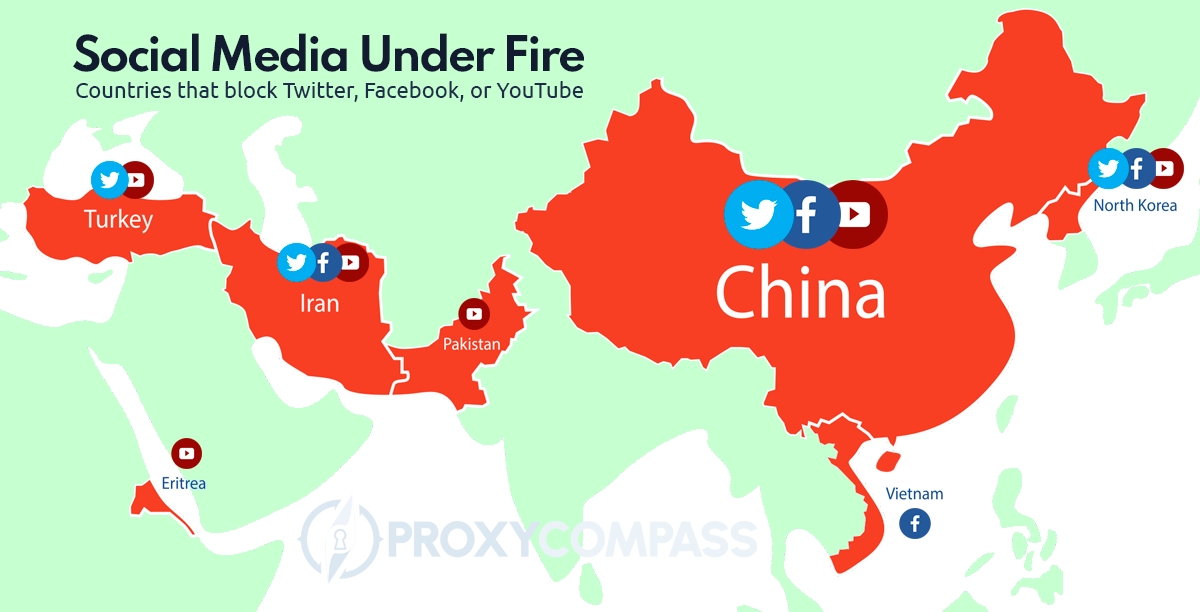
On Netflix, YouTube and other websites, certain content is only accessible to users from certain countries. Other websites such as LinkedIn are completely blocked in certain countries.
To ensure that users from “blocked countries” can see corresponding content or websites, they must “pretend” to the provider that they come from the “allowed” country. This can be achieved quite easily by using proxies.
Twitter and Facebook
Social networks such as Twitter and Facebook also block access to their content from different countries ̶ or these services are blocked in certain countries. For example, North Korea, Iran, China and many other countries force internet providers to block access to Twitter and/or Facebook.
The reasons for this are complex: many governments, especially in the Middle East and Asia, control information online for their citizens and want to stop the exchange (in a political context).
But also companies and schools often block access to social media sites in their internal networks. The main reasons cited are reduced productivity and an increase in the likelihood of cyberbullying and distraction.
However, Twitter and Facebook are not only used for personal purposes – many companies use these social media platforms as a marketing tool for communication with followers.
One and the same user therefore often manages many different accounts and/or company pages on Facebook/Twitter, which they usually try to block. With proxies these restrictions can be overcome. Proxies are therefore extremely useful for those who do online marketing on a large scale.
Proxies with Torrents
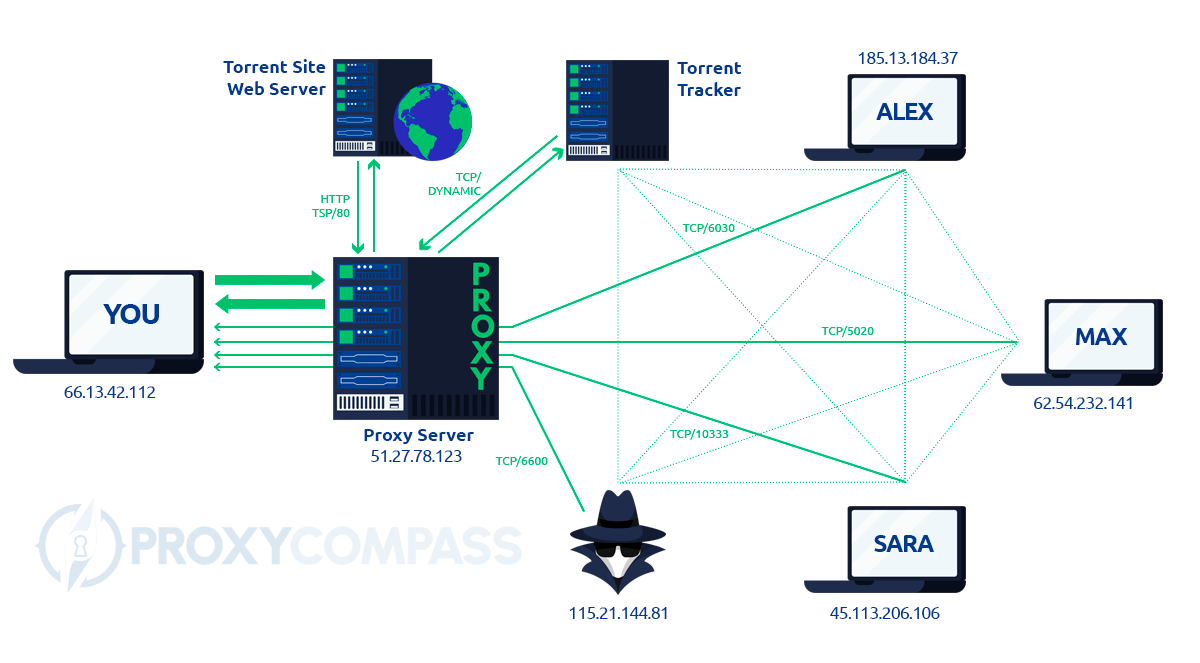
Torrents use a file-sharing programme such as BitTorrent, uTorrent or Vuze to download content (usually popular and therefore usually legally protected films, music, software, etc.) to your own computer.
However, data is also uploaded from your own computer and thus shared. In most countries this is prohibited, so users who download/sharing illegal content are liable to prosecution.
When you download/share a torrent, you connect to a variety of other users (also called a swarm). All users in the swarm can see the IP address of your machine. These often include monitoring groups paid by the entertainment industry to identify users who share illegal content. With the help of the IP address, the internet provider is then informed about the (criminal) activity of his customer and/or legal action is taken.
In order to avoid claims from copyright holders, Torrents also uses proxies, which are also used to hide the user’s IP address.
With the help of proxies, blocked or legally protected content can be accessed or downloaded “anonymously” from anywhere. And although proxy services do not approve of this, they cannot technically restrict it. Only after requests from copyright holders are received will accounts of such users be blocked.