Proxy servers generally serve to disguise one's own identity while browsing, but also serve as a cache where web pages and content can be cached. Proxies can be used effectively particularly in the area of cybersecurity and marketing – we will show you how this works in this article.
Proxy server to simulate DDoS attacks
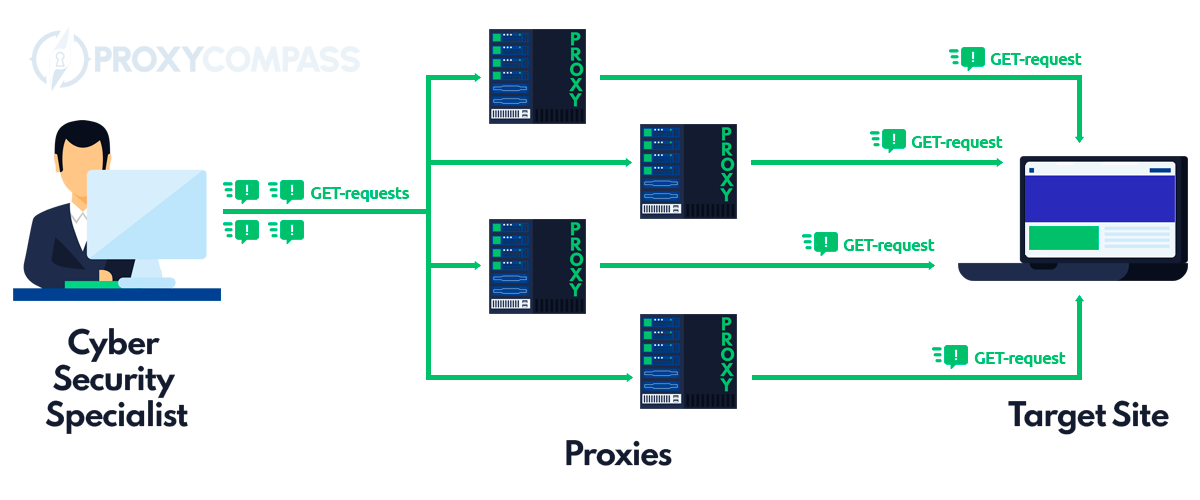
Every company is required to protect the data of its internal IT systems. In order to check the extent to which a company's IT infrastructure is secure, certain tests can be carried out – simulations of so-called DDoS attacks.
With a simulation of DDoS (short for Distributed Denial of Service) attacks with real IPs, systems can be tested for their resilience. In the process, a large number of targeted requests are made from numerous computers, which can lead to a server overload and paralyze services provided by the attacked party.
With such simulated attacks, important data can be obtained about the extent to which the sensitive IT system can withstand an attack and where the system needs to be further expanded in the area of cybersecurity so that important company data cannot be hacked.
Network and website monitoring
Especially in marketing, network and website monitoring is an important task and an integral part when analyzing how to make marketing strategies successful.
With proxies, marketing professionals can check how users from all regions of the world are using the site or even an app and how the service is performing. Using proxies, the region from which the website, app or network is accessed can be adjusted simply by changing the IP address, making it easy to see how a website can be accessed from different regions.
Is all content displayed? Is the loading time of the website fast? These important questions can be easily checked by this method; it will reveal where improvements are necessary.
Protection of company data
Proxy servers play a major role in protecting a company's internal data. Even small companies have to ensure that their IT systems are shielded against external attacks and data leaks are prevented by an adequate security system.
They are placed between the attacker's own system and any external access, thus acting as an extra hurdle that prevents the attacker from accessing the IT system directly.
In addition, proxy servers provide a certain degree of anonymity when surfing the internet and disguise your IP address. A new IP address is generated by the proxy server, and thus your own, real IP address is not revealed.
In addition, in many companies nowadays, it is quite common for employees to work from home, which presents new security risks for company data, as it is not always possible to ensure that employees' internet connection is secure. By using proxy servers, the risk can be minimized and the company data can be protected.